Edward Snowden the most wanted hacker, introduce a new app called Haven app. Let's reveal the real use of Haven. Snowden’s new app turns any Android phone into a surveillance system.
Table of Contents
ToggleWhat is Haven?
Haven is for people who need a way to protect their personal spaces and possessions without compromising their own privacy. It is an Android application that leverages on-device sensors to provide monitoring and protection of physical spaces. Haven turns any Android phone into a motion, sound, vibration, and light detector, watching for unexpected guests and unwanted intruders. We designed Haven for investigative journalists, human rights defenders, and people at risk of forced disappearance to create a new kind of herd immunity. By combining the array of sensors found in any smartphone, with the world’s most secure communications technologies, like Signal and Tor, Haven prevents the worst kind of people from silencing citizens without getting caught in the act.
We are announcing Haven today, as an open-source project, along with a public beta release of the app. We are looking for contributors who understand that physical security is as important as digital, and who have an understanding and compassion for the kind of threats faced by the users and communities we want to support. We also think it is really cool, cutting edge, and making use of encrypted messaging and onion routing in whole new ways. We believe Haven points the way to a more sophisticated approach to securing communication within networks of things and home automation systems.
How to use Haven?
Haven real use to monitor something really important. So download the app from the Google Play store.
First for use Haven as a surveillance device use any unwanted smartphone which is currently not in use. For setting a surveillance download and install it on the extra smartphone.
Once installed the device needs to be configured first the app use the following sensor for this surveillance system. The following sensors are monitored for a measurable change, and then recorded to an event log on the device:
* Accelerometer: phone’s motion and vibration
* Camera: motion in the phone’s visible surroundings from front or back camera
* Microphone: noises in the environment
* Light: change in light from an ambient light sensor
* Power: detect the device being unplugged or power loss
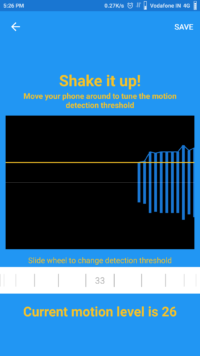
The configuration part is a little tricky the Motion sensor is the first sensor to be configured. You have to plan the device capability and what it is monitoring. If it’s a living thing u need to set up the motion level high if it’s a non-living thing set it to low. The device will show the current Motion level so why it is showing the current motion level you need to change the motion level to your wish and shake the phone to the peak level. So the device will detect the set the range. If the motion level is high and above the yellow line then it's in the danger level.
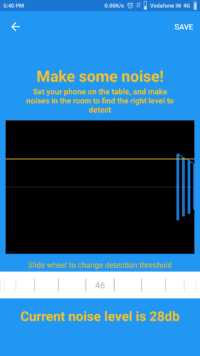
Then the second part of the configuration part is setting up the Noice level, set the noise level y sliding the wheel and set the detection threshold check, and make some noise whether the app detecting the threshold noise level.
Note you cannot change the threshold level below the current detecting value so configure it when no one is around you.
The final part of the configuration is to set your phone number and get notified of intrusion events instantly and access the logs remotely.
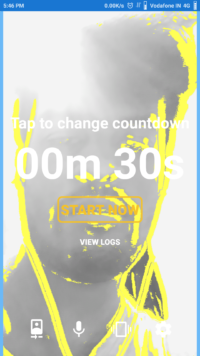
Once done the surveillance it almost ready. Then click on the start button to enable the surveillance system
To access this app from distance you have to enable the option called Remote access via Tor Onion Service.
Tor onion service makes it possible for users to hide their locations while offering various kinds of services, such as web publishing or an instant messaging server. Using Tor "rendezvous points," other Tor users can connect to these onion services, formerly known as hidden services, each without knowing the other's network identity, click here to find more about Tor.
Once the Tor service configured, Give the service address and password in the field.
Disadvantage of this app
The configuration part of this app is very tricky and difficult to understand for normal people and getting remote access from tor is way more difficult. There are a lot of configuration steps to follow.
And moreover, I don’t see any real practical application of Haven.



Why haven’t you linked the setup instructions for remote access? ive been searching for awhile and can’t find them, not in haven support, not anywhere… if they do exist, and you have seen them, would you please link? and maybe email me letting me know you have…
as for practical applications, anyone who needs to monitor a space, such as their home, business, studio, political spaces, etc, from intrusion, but doesn’t have the resources to buy fancy surveillance systems, could find this useful….