Security is the main concern when we browse through the Internet, to take care of these security things there are lot of Security protocols, in that TLS and SSL are the main. TLS abbreviated as Transport Layer Security. TLS is a cryptographic protocol that provides end-to-end communications security over networks and it is widely used for internet communications and online transactions. And TLS is a more secure and efficient protocol compare to SSL, it has stronger message authentication, key material generation, and other encryption algorithms. For example, TLS supports pre-shared keys, secure remote passwords, elliptical-curve keys and Kerberos whereas SSL does not. So you may wonder how the TLS works, The working principle is very simple The TLS protocol specification defines two layers.
1.The TLS record protocol–> provides connection security.
2.The TLS handshake protocol–> Enables the client and server to authenticate each other and to negotiate security keys before any data is transmitted.
In these TLS record protocols Secures the application data using the keys created during the Handshake. The Record Protocol is responsible for securing application data and verifying its integrity and origin. It manages the following:
- Dividing outgoing messages into manageable blocks and reassembling incoming messages.
- Compressing outgoing blocks and decompressing incoming blocks (optional).
- Applying a Message Authentication Code(MAC) to outgoing messages, and verifying incoming messages using the MAC.
- Encrypting outgoing messages and decrypting incoming messages.
When the Record Protocol is complete, the outgoing encrypted data is passed down to the Transmission Control Protocol (TCP) layer for transport. Transport handshake Protocol is a multi-step process, Handshake Protocol is responsible for the authentication and key exchange necessary to establish or resume secure sessions. When establishing a secure session, the Handshake Protocol manages the following:
- Cipher suite negotiation
- Authentication of the server and optionally, the client
- Session key information exchange.
This multi-step process is a little complex that the record protocol, in TLS, a server provides an identity to the client by the use of public and private key pairs, Then the session key has been generated and shared between client and server, then the main part is establishing a secure session by using TLS, In this client and server exchanges the simple hello messages with encryption keys. Also for each message ends client and server gets a certificate of authentication and finish the handshake process, This session ID will be saved for future use so that This TLS session can be resumed in the future. These are the basic working principle of TLS. The IETF officially took over the SSL protocol to standardize it with an open process and released version 3.1 of SSL in 1999 as TLS 1.0. The protocol was renamed TLS to avoid legal issues with Netscape, which developed the SSL protocol as a key feature part of its original Web browser. Then TLS 1.1 was added with little extra features, TLS 1.2 is the current version of the protocol, this guide will help you to Disable TLS Setting in Windows, So without wasting any time we jump into the topic. Usually to disable the TLS setting we follow the below mention Standard method from the Internet setting, sometimes this method won’t be effective so we created a script to disable TLS setting, follow the methods below.
Method 1: Disable TLS setting using Internet settings.
- Open Internet Explorer
- Open the Tools menu (select the cog near the top-right of Internet Explorer 10), then choose Internet options
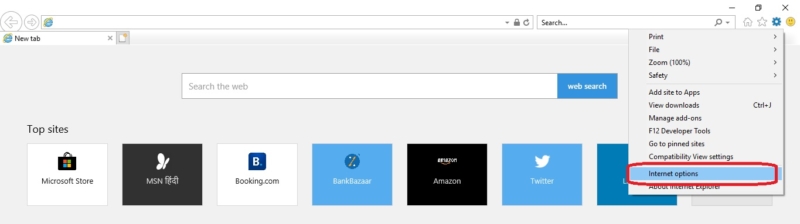
- Select the Advanced tab.
- Scroll down to the Security section at the bottom of the Settings list.
- Select Use TLS 1.1 and Use TLS 1.2.
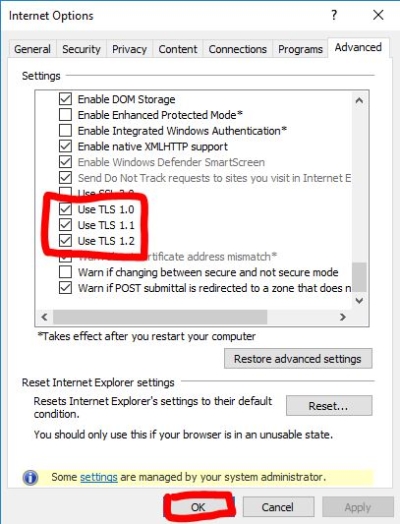
- For extra security, deselect Use SSL 3.0. When complete, your settings should match the following:
Selected: Use TLS 1.0, Use TLS 1.1 and Use TLS 1.2 Not selected: Use SSL 2.0 and Use SSL 3.0
- Select Apply and OK.
Method 2: Disable TLS settings using Registry Editor.
- Open Run command by pressing Windows + R and type Regedit and hit enter.
Navigate to the following path. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
- Once you followed the path you can see Three or maybe four folders under Protocols, TLS1.0, TLS1.1, TLS1.2, If you expand these folders you can see the client and server folder.
- If you want to disable TLS1.0 expand the TLS1.0 and click on the client folder from the right-hand side you can see two D-Word values DisabledByDefault and Enabled. To enable or disable this TLS right click on the D-Word value and modify it.
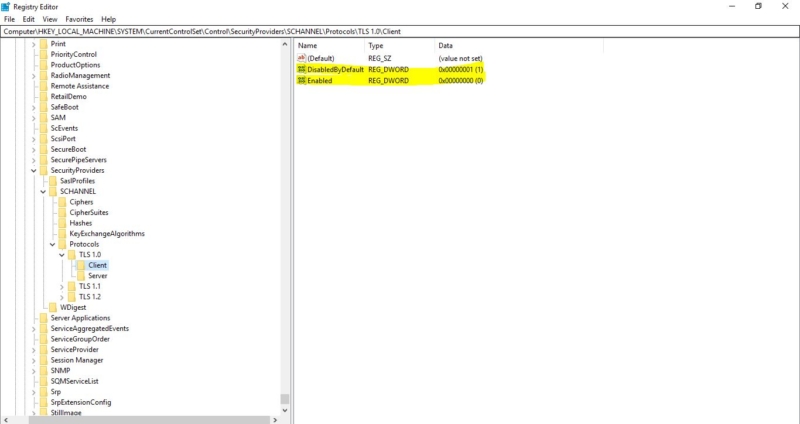
To Enable:
DisabledByDefault –>0 Enabled –>1
To Disable
DisabledByDefault –> 1 Enabled –> 0
- Once done restart the system to make it effective.
Note: To disable all the Three TLS versions, proceed with these steps for another Two(TLS 1.1 and TLS 1.2). If you are facing any difficulties to modifying these values download the Reg file from below Link and merge it.
- After merging the TLS restart the PC once to make it effective.
Method 3: Disable TLS setting using PowerShell
- This method is similar to the previous method, What it do is the same like reg edit method but the entire process is handled by the PowerShell.
- Open Power Shell ISE in run as admin mode.
Copy and paste the below mention code.
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.0 has been Disabled.'
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.1 has been Disabled.'
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 has been Disabled.'
- And save it as DisableTLS.ps1, This code is for disabling the TLS. If you don’t want the code editing stuff just download the script below from the given link.
Note: Before Running these scripts make sure you Enabled the execution of scripts is enabled, if you are not click here to know more about it. If you didn’t Disable these restrictions in PowerShell you will get the below-mentioned error.
File C:\Common\Scripts\Basescript.ps1 cannot be loaded because the execution of scripts is disabled on this system. Please see “get-help about_signing” for more details. At line:1 char:13 + .\Basescript.ps1 <<<< + CategoryInfo : NotSpecified: (:) [], PSSecurityException + FullyQualifiedErrorId : RuntimeException



I think you have the flag logic backward in the script files. for DisabledByDefault should be 1 and Enabled = 0 for disabling.