NTLM stands for NT LAN Manager (New Technology LAN Manager), it is a collection of Security Protocols Which is created by Microsoft. NTLM is a Challenge-response authentication protocol that is used to authenticate a client to a resource in the Active Directory domain. This protocol allows various computers and servers to mutual authentication. When the client sends request access to a service associated with a domain, the service will immediately send a challenge to the client. This challenge includes mathematical operations, so the client needs to perform a mathematical operation using its authentication token. Once the client returns the result of the operation, the source service may validate the result or send it to the Domain Controller (DC) for Validation. Once the Service or DC confirms that the client’s response is correct then the service will give access to the Client.
NTLM is a type of single sign-on (SSO) because it allows the user to provide the underlying authentication factor only once during the login. Due to the Vulnerabilities, the NTLM is considered Insecure. Because it uses outdated cryptography and it leads to several modes of attacks. Mainly NTLM is not recommended by Microsoft and it is replaced with Kerberos protocol, it is vulnerable to the pass the hash attack and brute-force attacks. So it is better to deactivate this service, this article will guide you to Disable NTLM Authentication in Windows Domain.
Disable NTLM Authentication in Windows Domain:
You can disable the NTLM authentication protocol using two different methods, follow the below-mentioned methods to disable it.
Using Group Policy Editor:
Open Run command by pressing Windows + R and type gpedit.msc and hit enter. This command will open the Group Policy Editor.
Now Navigate to the following path.
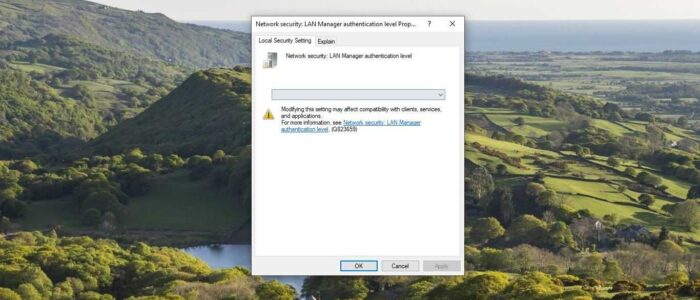
Computer Configuration > Windows Settings > Security Settings > Local Policies > Security OptionsFrom the left-hand side click on the Security Options and from the right-hand side look for the policy named Network Security: LAN Manager authentication level.
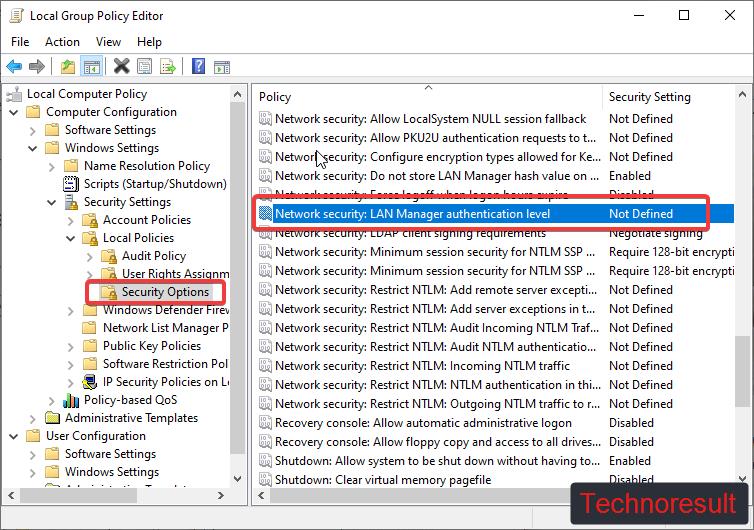
Double click on the Network Security: LAN Manager authentication level policy and open the policy settings.
Click on the Local Security Settings tab and click on the drop-down menu and choose Sent NTLMv2 response only or Refuse LM & NTLM.
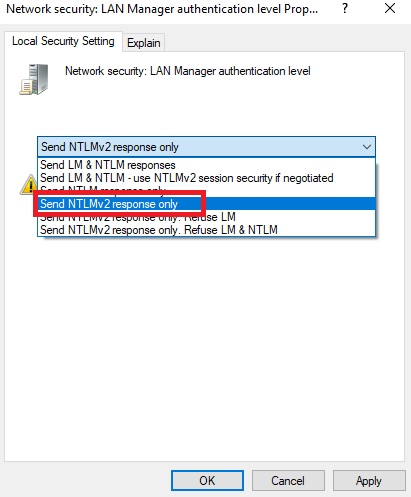
Click on Apply and OK. And restart the system once, this will disable the NTLM authentication.
Using Registry Editor:
Note: Modifying the Registry is risky, and it causes irreversible damage to your OS Installation Follow the steps correctly. Friendly advice Before Modifying Registry Creating Restore Point is recommended.
Open the Run command by pressing Windows + R and type Regedit and hit enter. This command will open the Registry Editor Console.
Now Navigate to the following path.
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Lsa
From the left-hand side, right-click on the Lsa Registry keyword and choose New > DWORD (32-bit) Value. Name the DWORD as LmCompatibilityLevel and click on OK.
Double click on LmCompatibilityLevel and set the Value data to 5. The value corresponds to “Sent NTMLv2 response only. Refuse LM & NTLM”.
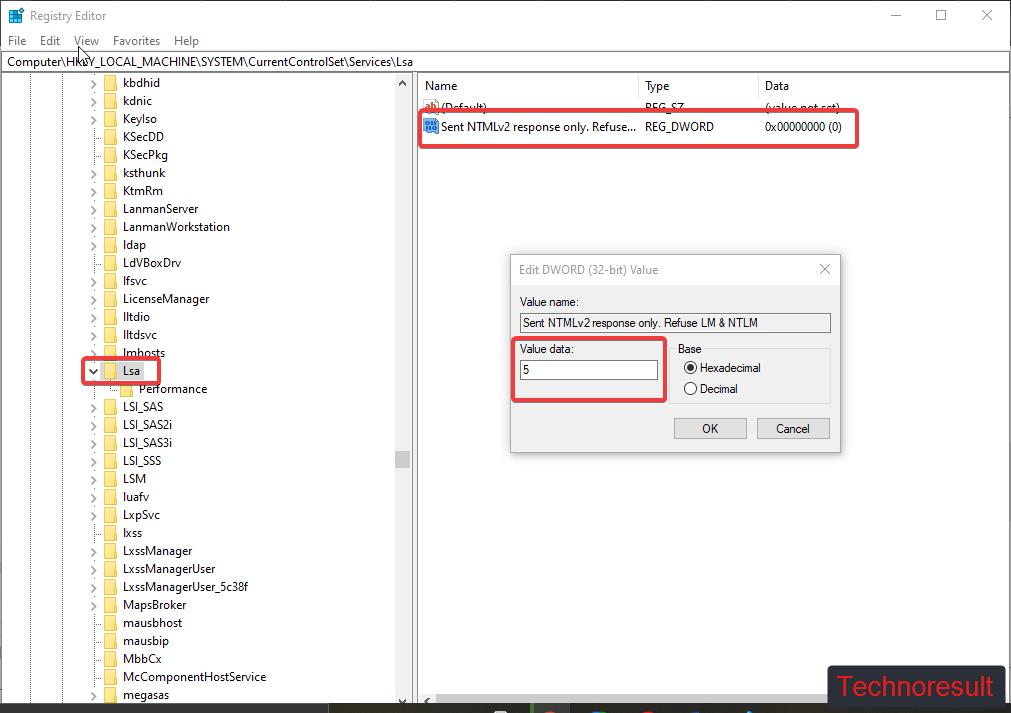
Click on Ok and Close the registry editor. This will disable the NTLM authentication.
Read: Fix Unable to Click on Taskbar issue in Windows 10