Bitlocker is a feature that protects your hard disk from external attacks or from offline attacks. It is a full volume encryption feature included with Microsoft Windows (Pro and Enterprise only) versions starting with Windows Vista. It is designed to protect data by providing encryption for entire volumes. By default, it uses the AES encryption algorithm in cipher block chaining (CBC) or XTS mode with a 128-bit or 256-bit key. This encryption algorithm is strong enough to protect your HDD and your data. For example, if your HDD is encrypted and you lost your HDD and if someone tries to access your data without the Recovery key then they can’t get anything. BitLocker also protects your data if a malicious user boot from an alternate Operating System. With either attack method, BitLocker encrypts the hard drive so that when someone has physical access to the drive, the drive is unreadable. There is one more feature Microsoft includes along with the Bitlocker, that is Bitlocker PIN or Pre-Boot Pin Pre-boot authentication with full-disk encryption products (including BitLocker) is a process that requires a user to authenticate prior to making the contents of the system drive accessible.
In the case of BitLocker, BitLocker encrypts the entire drive, including all system files. BitLocker accesses and stores the encryption key in memory only after a user provides a specific PIN or USB startup key. Most of the companies have encrypted their Computers HDD with Bitlocker, Also some organization set policy to automatically encrypt their HDD and they applies Pre-Boot PIN or Bitlocker PIN to boot the system. This is an additional feature that comes along with the Pre-Boot PIN. Once you set the Pre-boot PIN you have to boot the system with the PIN without the PIN you can’t boot the system and if someone enters the wrong PIN so many times the system will ask for the BitLocker Recovery key. You can set the PIN easily with the help of the Bitlocker Drive Encryption option from the Control panel. By default in Windows 10 users are allowed to change the BitLocker PIN or Password. If you don’t want standard users to change the BitLocker PIN then this article will guide you to Restrict Standard Users from Changing Bitlocker PIN in Windows 10.
Steps to Restrict Standard Users from Changing Bitlocker PIN:
Open Run command by pressing Windows + R and type Gpedit.msc, This command will open the group policy editor.
Now navigate to the following location.
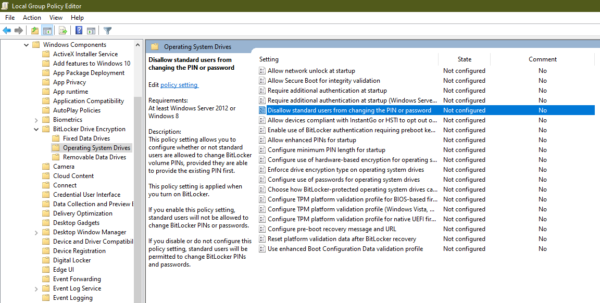
Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives
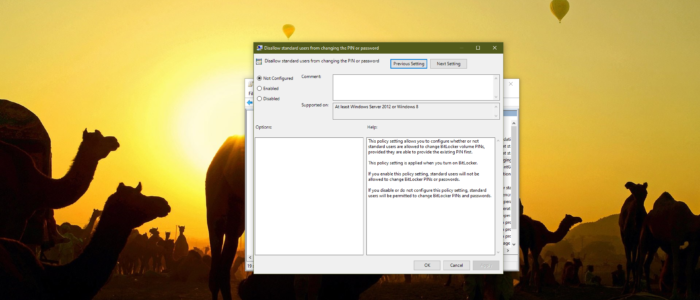
Click on the Operating System Drives from the left-hand pane search for Disallow Standard users from changing the PIN or Password.
Click on the Policy setting to edit of Disallow Standard users from changing the PIN or Password. This policy setting allows you to configure whether or not standard users are allowed to change BitLocker volume PINs, provided they are able to provide the existing PIN first. This policy setting is applied when you turn on BitLocker. If you enable this policy setting, standard users will not be allowed to change BitLocker PINs or passwords. If you disable or do not configure this policy setting, standard users will be permitted to change BitLocker PINs and passwords.
You can see three Options: To Enable Standard Users from Changing Bitlocker PIN Select the Not Configured or Disabled and click OK To Restrict Standard Users from Changing Bitlocker PIN
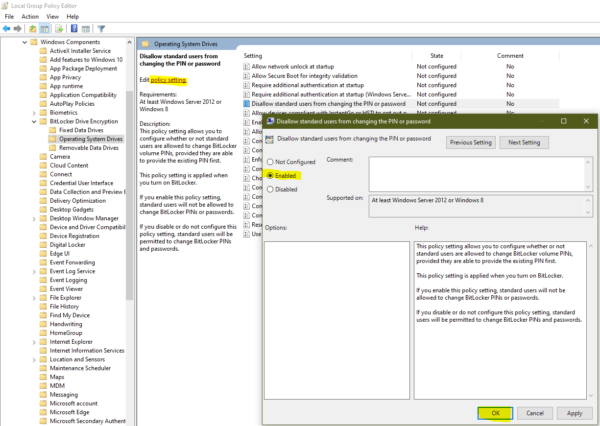
Select the radio button for Enabled and click OK. Once you Enabled these settings click on OK and Restart the machine to make it effective.
Read Also:
How to Enable Bitlocker using PowerShell in Windows 11?