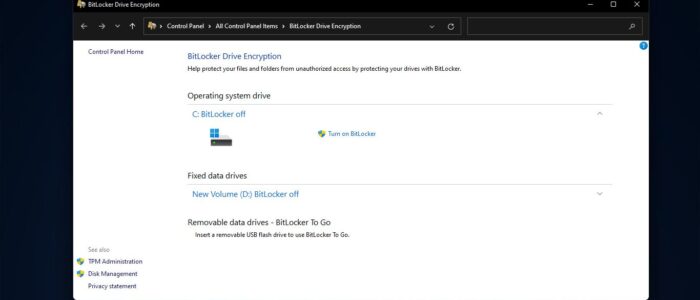
Bitlocker is a feature that protects your hard disk from external attacks or from offline attacks. It is a full volume encryption feature included with Microsoft Windows (Pro and Enterprise only) versions starting with Windows Vista. It is designed to protect data by providing encryption for entire volumes. By default, it uses the AES encryption algorithm in cipher block chaining (CBC) or XTS mode with a 128-bit or 256-bit key. This encryption algorithm is strong enough to protect your HDD and your data. For example, if your HDD is encrypted and you lost your HDD and someone tries to access your data without the Recovery key, they can’t get anything. BitLocker also protects your data if malicious user boots from an alternate Operating System. With either attack method, BitLocker encrypts the hard drive so that when someone has physical access to the drive, the drive is unreadable. Mostly BitLocker is used by corporate users and BitLocker is considered as one of the main compliance parameters in many corporate companies. By default, Windows allows users to encrypt and decrypt HDD, both the process requires admin privileges. Most of the users have admin privileges by default and using admin privileges users may have a chance to decrypt their Hard Disk. If you’re an IT administrator and want to prevent Users from Decrypting BitLocker in Windows 11, this article will guide you to achieve it using App locker rule.
Related: Fix Too many PIN entry attempts BitLocker error in Windows 10
Prevent Users from Decrypting BitLocker:
Open Run command by pressing Windows + R and type services.msc and hit enter. This command will open the Services Management Console.
Under Services snap-in look for the service named Application Identity, Make sure this service is running, if not Start the Application Identity service.
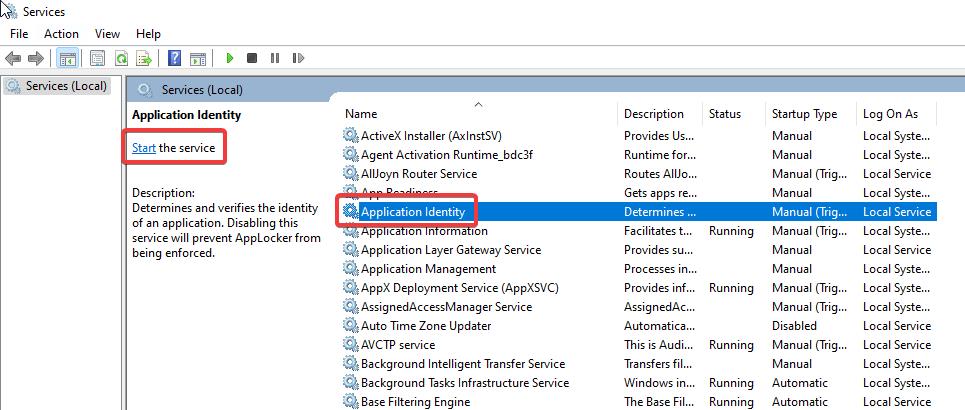
Once the service is started then, open the run command and type secpol.msc, and hit enter. This command will open the Local Security Policy snap-in.
Next, navigate to the following path.
Security Settings > Application Control Policies > AppLocker > Executable Rules
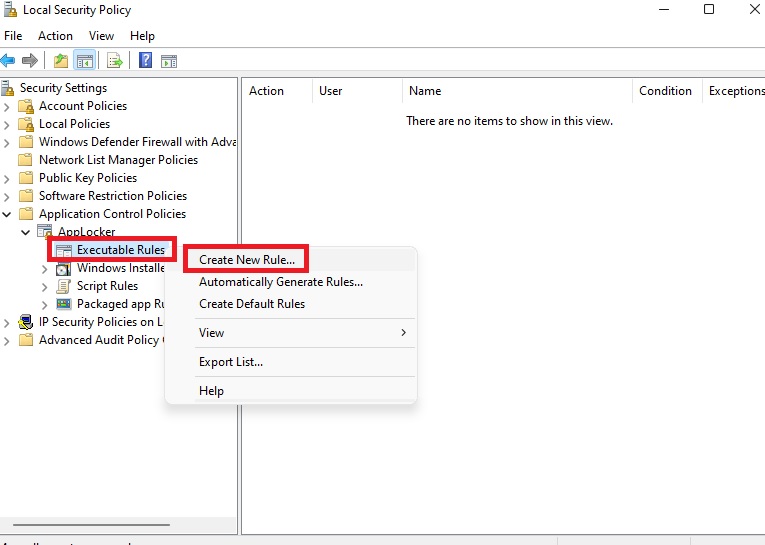
From the left-hand side right click on the Executable Rules and choose Create New Rule.
Under the Permissions window, from the left-hand side choose Permissions, and from the right-hand side, under Action choose Deny.
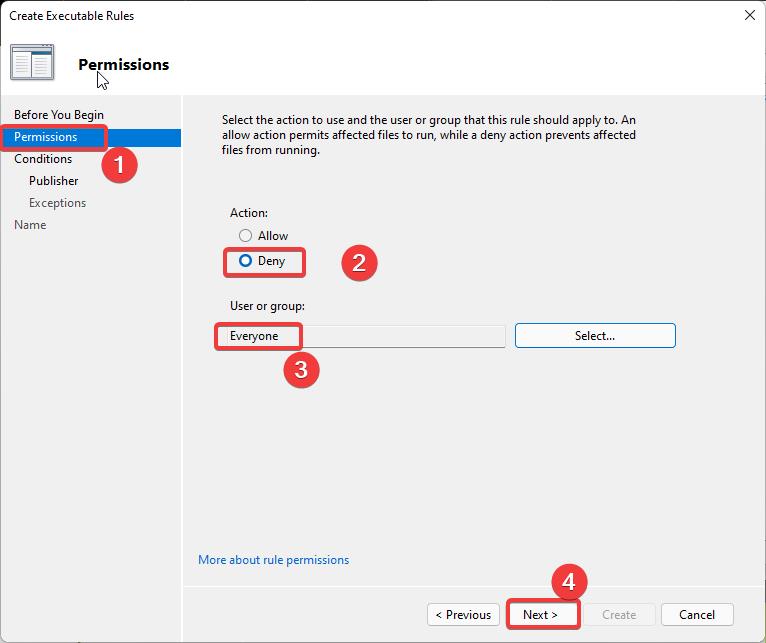
Under User or Group, choose Everyone, if you want to restrict only for specific user click on select and choose the user ID. Click on Next.
Select Publisher for the primary condition and click on Next.

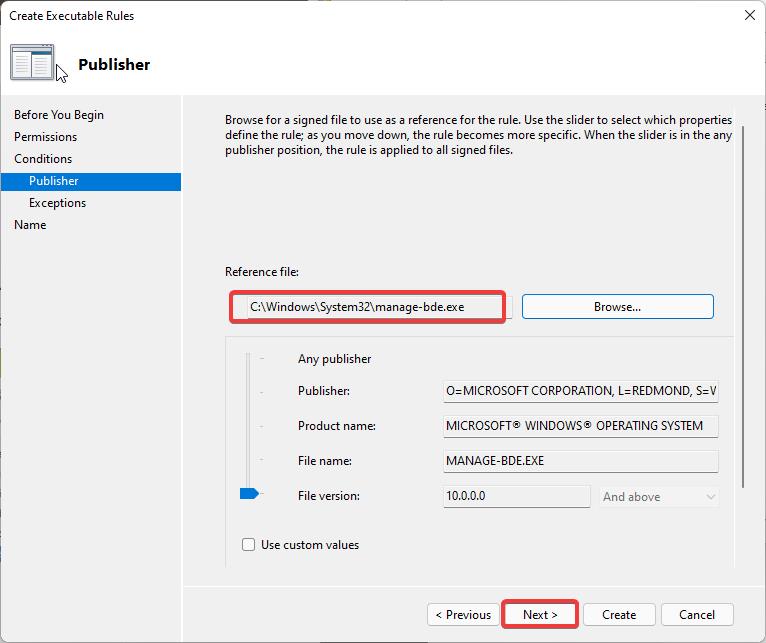
Next you need to choose the Reference file, click on the browse button and navigate to the following path.
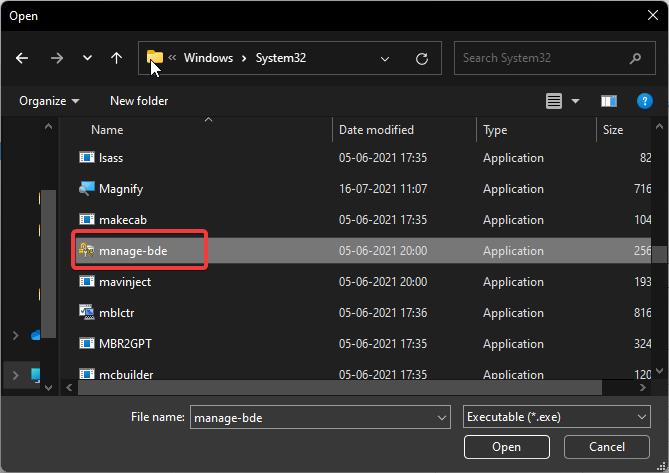
C:\Windows\System32
Under System32 look for manage-bde.exe and choose it, then click on next.
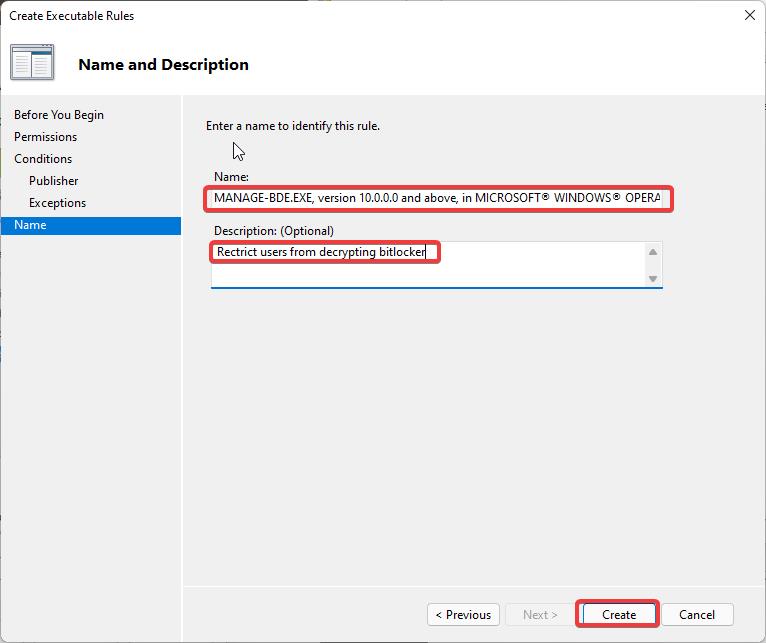
Under Name, give any name you and want and give a description, then click on create.
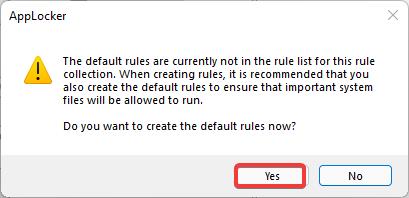
Now you’ll get an AppLocker warning prompt, click on Yes and proceed.
That’s it the rule has been successfully created. Close the Security policy console and open the command prompt and type gpupdate /force.
This rule will restrict users from decrypting the BitLocker, so whenever users try to turn off the BitLocker they will receive the Access denied error.
Read Also:
How to Restrict Standard Users from Changing Bitlocker PIN in Windows 10?
How to Enable Bitlocker using PowerShell in Windows 11?
Fix The Group Policy Settings for BitLocker startup options are in conflict